Token generation
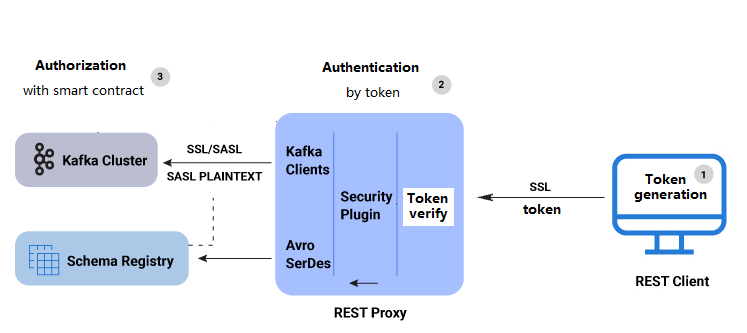
In first step, the token is generated by the client self without retrieveing from the authen server. It is one important feature for anonymous authentication. Anonymous authentication typically involves allowing users to access a system or service without requiring them to provide explicit credentials such as a username and password. However, the concept of generating authentication tokens without involving an authentication server contradicts some fundamental principles of secure authentication. If the client generates its own authentication tokens without involving a central authority (like an authentication server), it can introduce significant security risks and chanllege.
-
Security Concerns: Authentication tokens should be generated securely to prevent unauthorized access. If clients generate tokens on their own, there's a higher risk of vulnerabilities and insecure practices leading to token compromise.
-
Lack of Identity Verification: Authentication servers are responsible for verifying the identity of users before issuing authentication tokens. If clients generate their own tokens, there is no external authority ensuring that the client is who they claim to be.
-
Replay Attacks: Without a central authority managing token issuance and validation, it becomes more challenging to prevent replay attacks, where an attacker intercepts and reuses a valid token to gain unauthorized access.
-
Revocation Challenges: Revoking access for a specific user becomes problematic without an authentication server. If tokens are self-generated, there's no straightforward way to invalidate or revoke a compromised token.
-
Scalability Issues: In a system with a large number of users, managing authentication centrally allows for better scalability. If each client generates its own tokens, it becomes harder to manage and scale the authentication process.